Scale Least Privilege
Secure Cloud Identities
Streamline permissions management to Cloud, SaaS, and DBs. Ensures access remains secure, compliant, and agile.
Trusted by forward-thinking security teams











The switch to cloud has made
identity the new security perimeter
Manually managing permissions in a dynamic Cloud with an agile workforce increases security risks compliance gaps inefficiencies.
Modern Environments Requires Modern Approach
Axiom is an identity Security platform that helps organizations streamline their least privilege journey by discovering, remediating, provisioning, and automating permissions to Cloud & SaaS environments.
CIEM

UAR

PAM/JIT
Automate
/Delegate
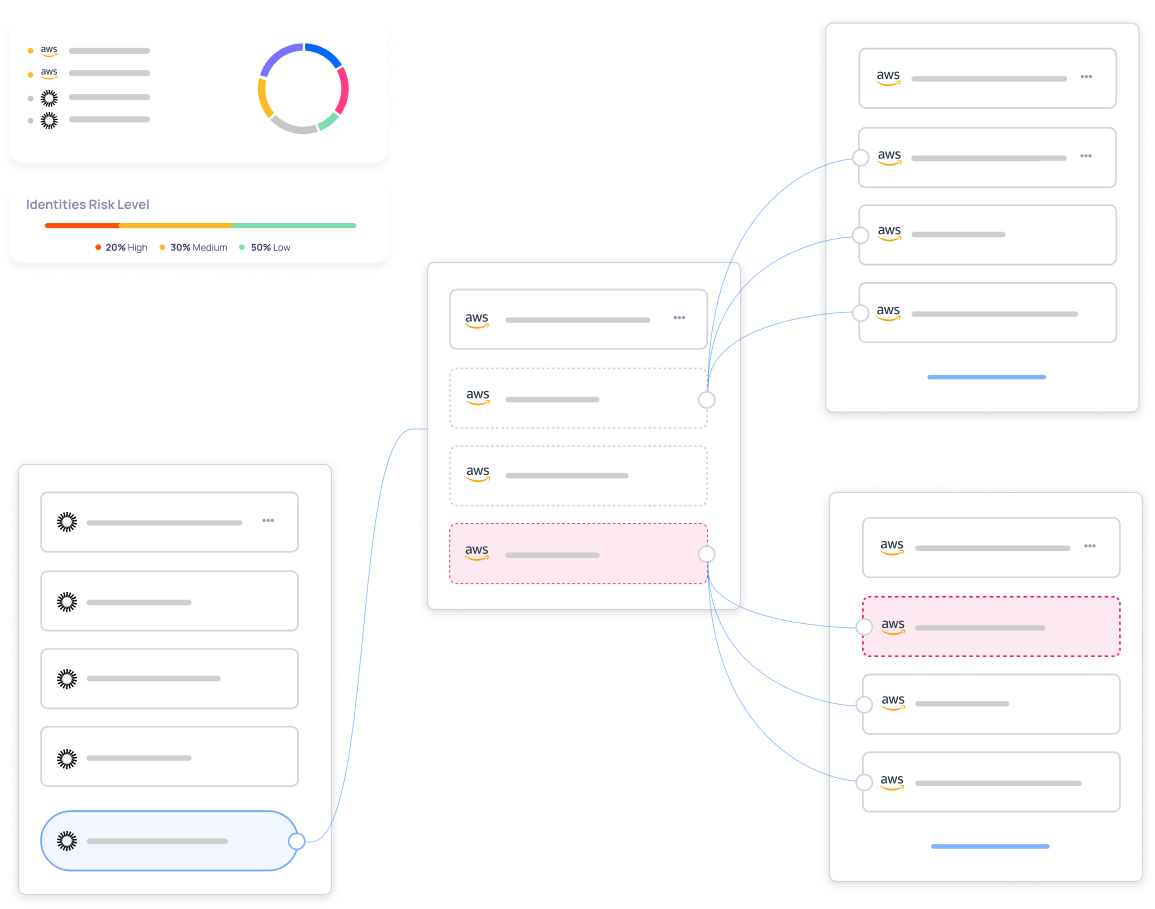
CIEM - Cloud Infrastructure Entitlement Management
Govern identities by discovering and remediating access risks, such as overprovisioned and unused permissions, toxic combinations, and privilege escalation.
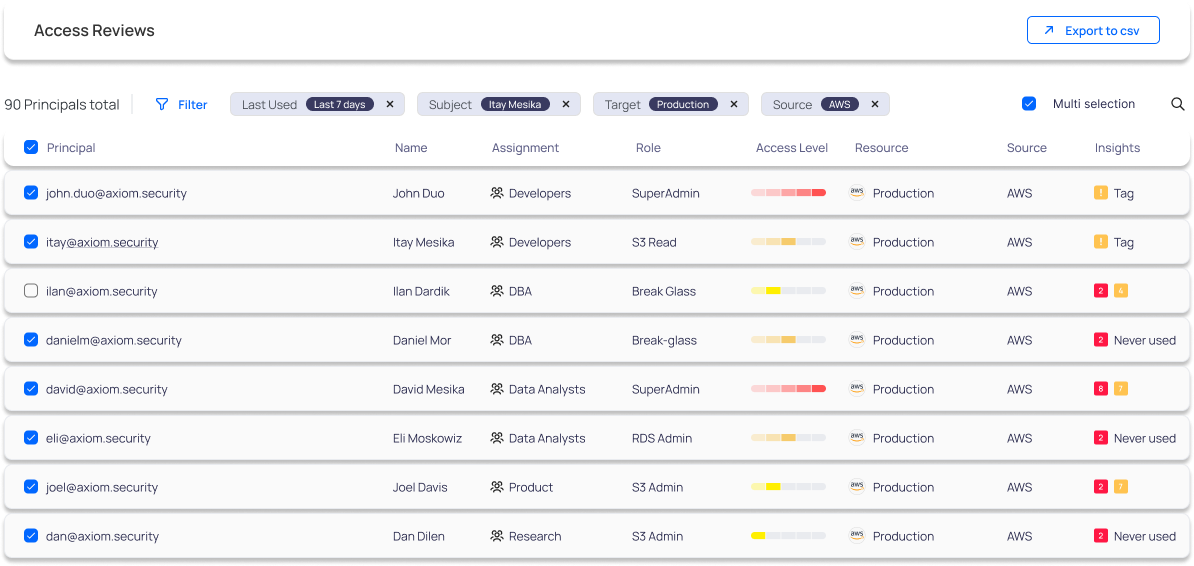
UAR - Streamlined User Access Reviews
Easily manage and orchestrate SOX, SOC-2, ISO, and HITRUST user access reviews, simplifying compliance and governance tasks around access control, saving your Ops and GRC teams time.
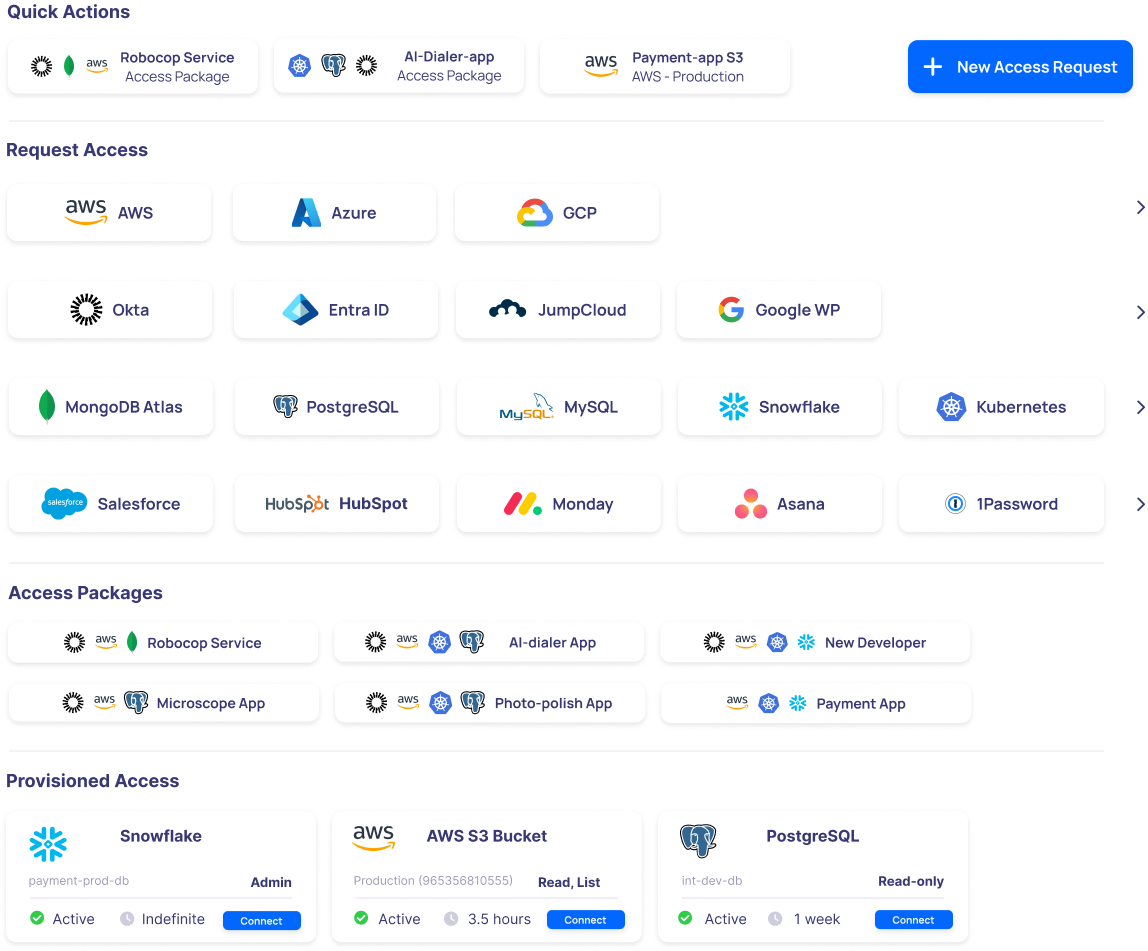
PAM / Just-In-Time - Least-Privileged Access Management
End users can efficiently and securely request access to various resources through self-service access requests that are tightly integrated with popular collaboration tools.
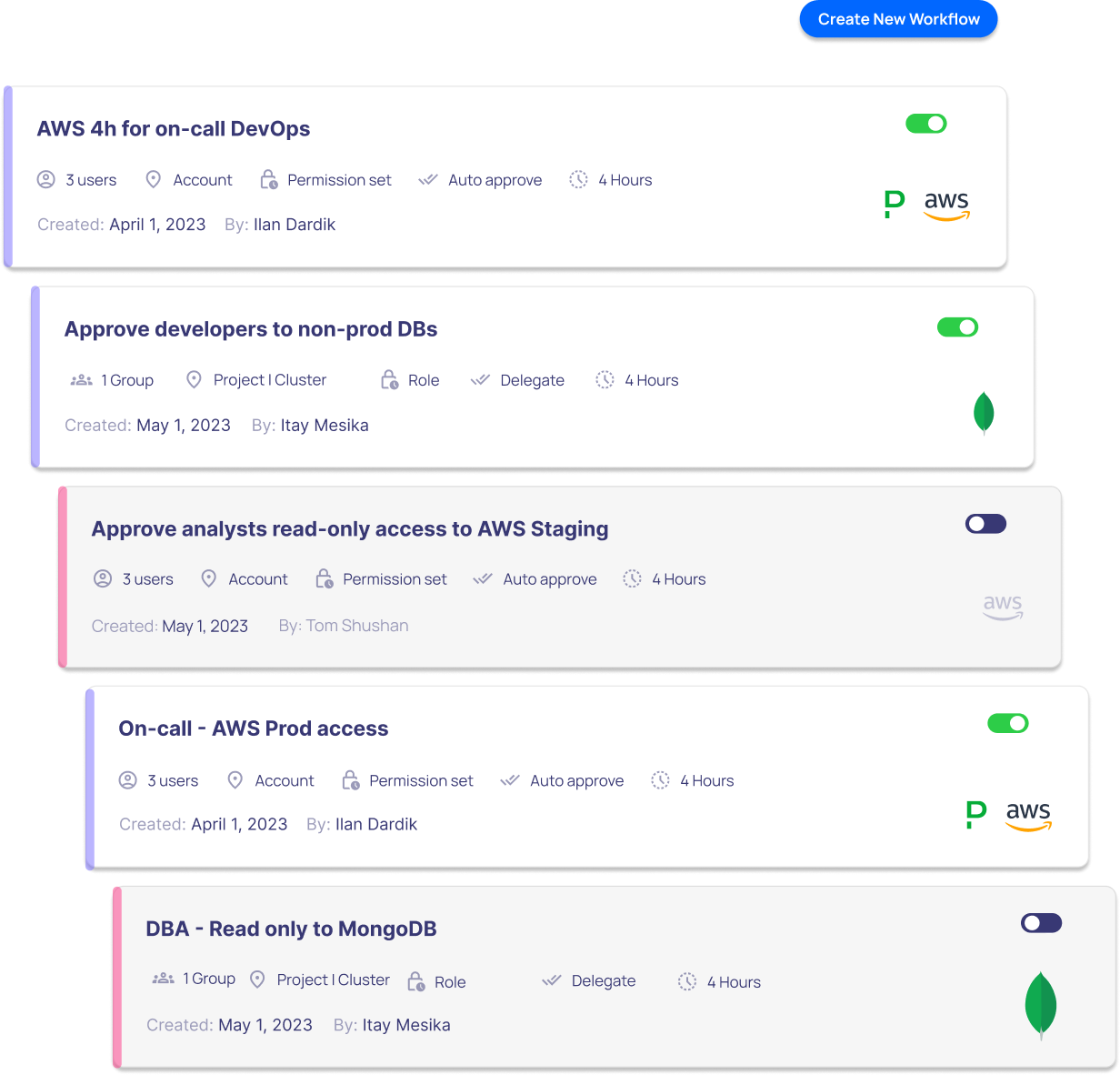
Automate or Delegate Grants
Automate routine, low-risk access requests and delegate sensitive ones to resource owners for fast approval. Set up advanced automation rules defining user eligibility, resource access, request conditions, and specific actions to be taken.
“There is something magical about setting up secure by default least privileged IAM workflows and getting out of the way to reduce risks without giving up on developer productivity.”

Axiom enabled us to transition to a secure and simplified permissions management model smoothly, ensuring each team member had precisely the access they needed, exactly when they needed it, with robust approval processes and auditable trails in place."

“Besides solving some of the most common security challenges associated with complex environments and IAM, Axiom became an organization accelerator for Truework's data engineering and development teams. With Axiom's assistance, Truework streamlined and enhanced its access management method, making it sleeker and safer."















