Automated Identity Security Platform
Axiom Security is an Identity security platform that streamlines the least-privilege journey by discovering, remediating, provisioning, and automating permissions to Cloud-native environments. Combining CIEM, PAM, IGA, and ITDR into a centralized ISPM solution ensures that organizations remain secure, compliant, and agile in today's rapidly evolving cloud and remote work landscape.
Discover
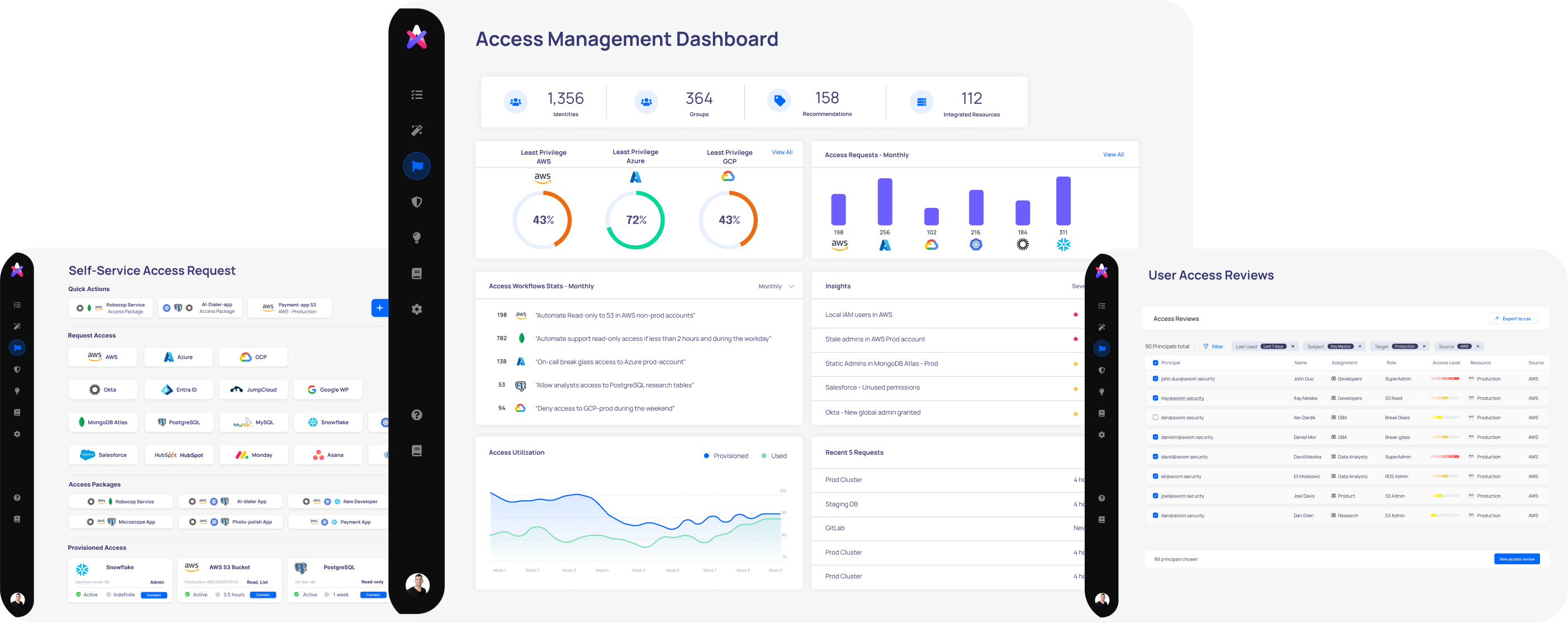
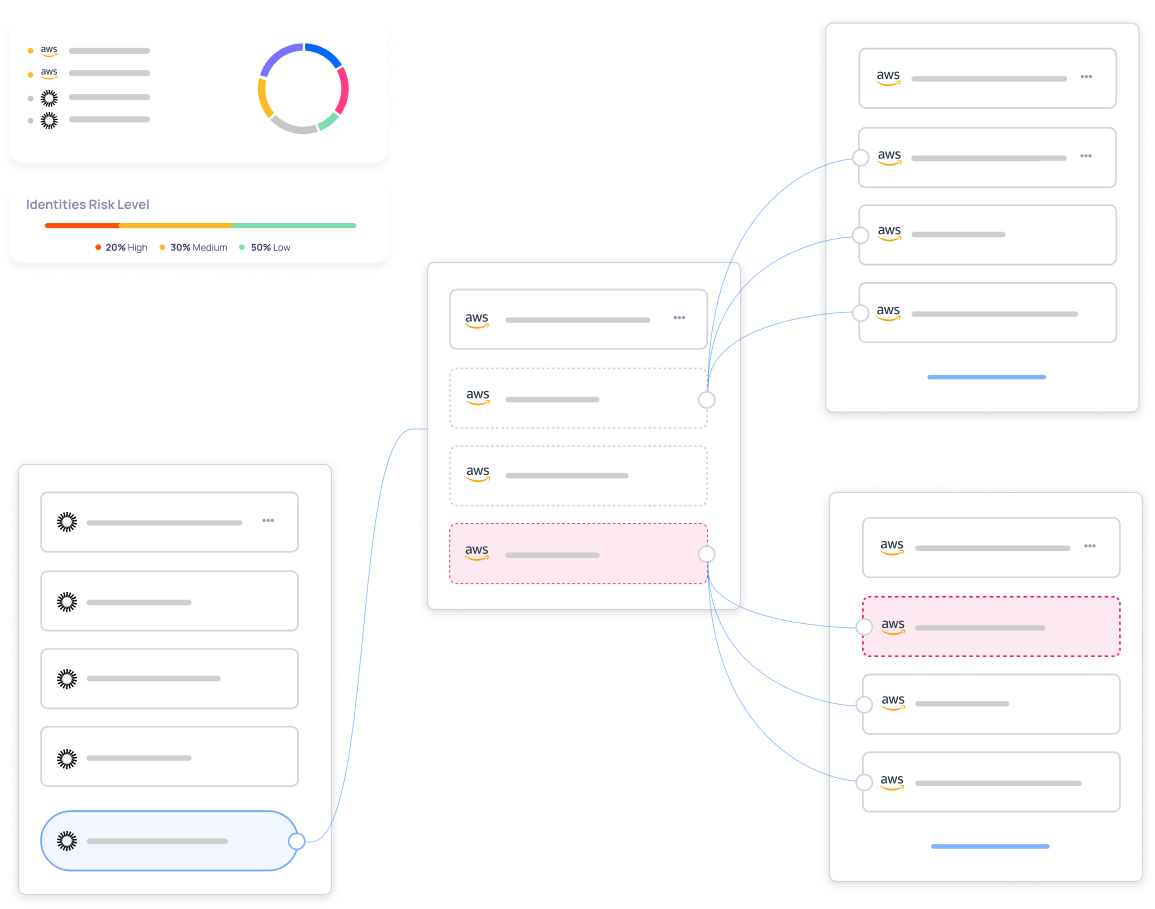
Centralized Entitlement Visibility
Monitor and control over-privileged access to see who has access to what across multiple environments. Axiom provides a panoramic view of access privileges within your organization. We simplify governance by allowing admins to identify and resolve access risks like overprovisioned permissions and potential privilege escalation.
You can also easily navigate the complex landscape of users, groups, and resources with our graph and inventory views. We provide detailed oversight of all administrative actions in our system events and logs, providing a comprehensive audit trail to ensure compliance.
Remediate
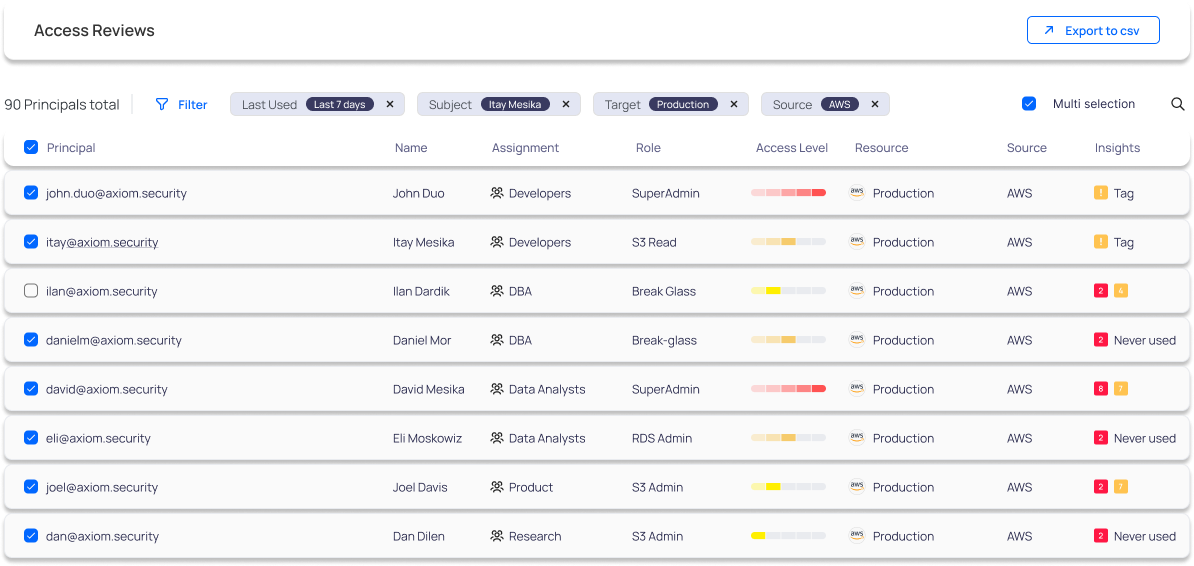
Automated User Access Reviews
Simplify your compliance and governance processes with a user-friendly platform designed to manage and orchestrate user access reviews for SOX, SOC-2, ISO, and HITRUST.
By streamlining these crucial tasks, our solution not only enhances your access control but also saves valuable time for your Operations and Governance, Risk, and Compliance (GRC) teams. With Axiom Security, you can ensure your organization meets stringent regulatory standards with efficiency and ease.
Provision
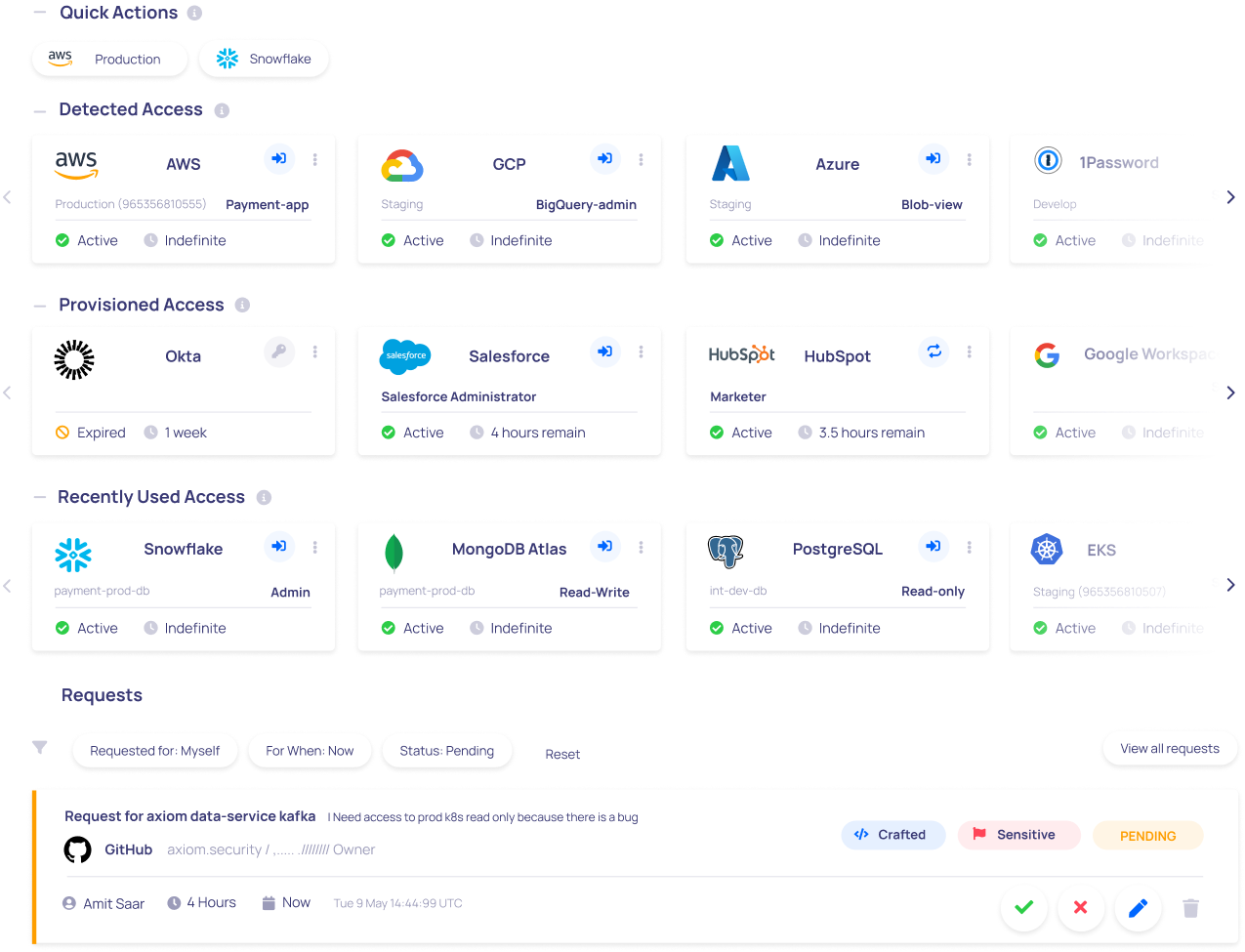
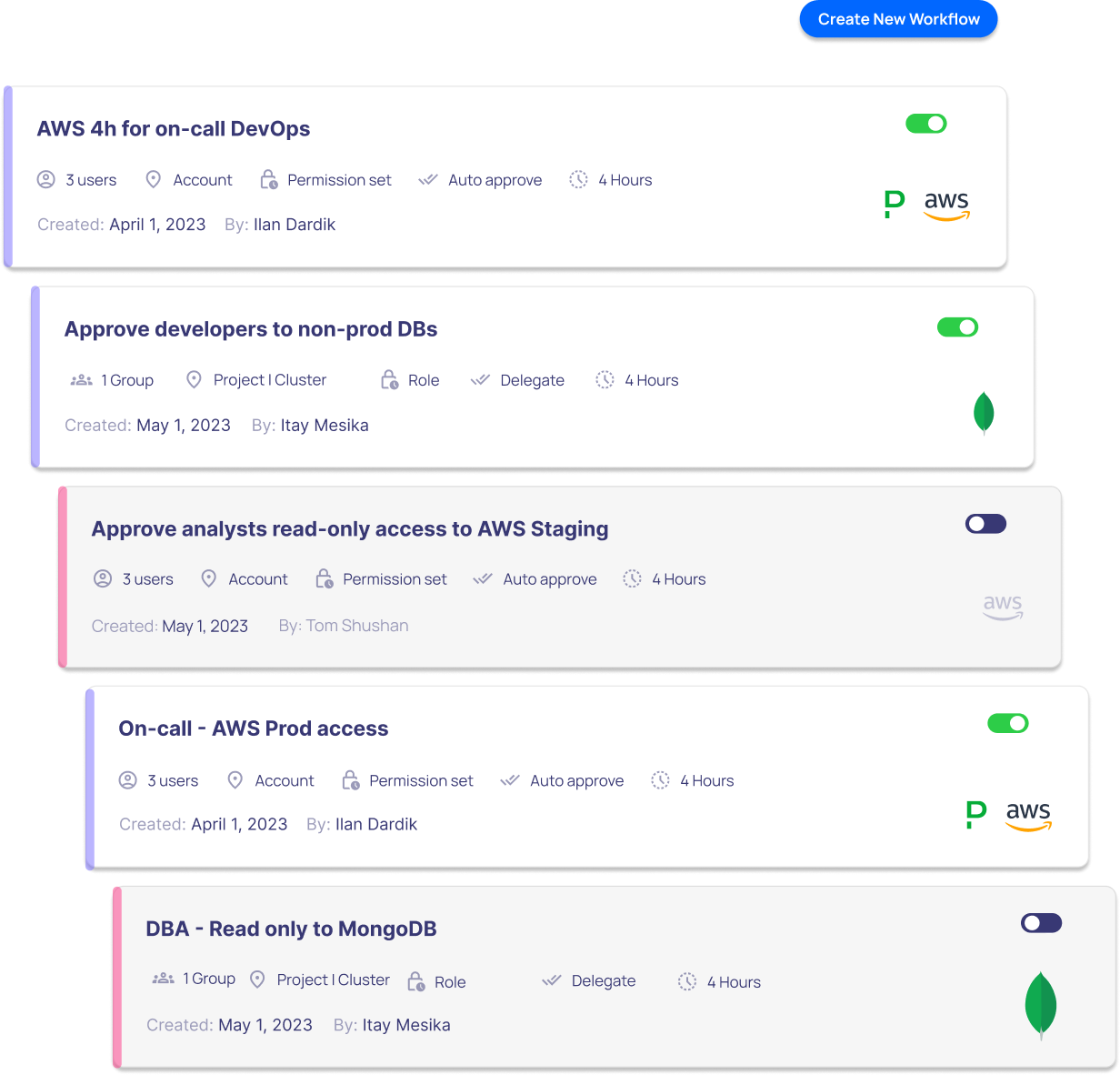
Scale
Automate or Delegate Access Grants
Rapid Deployment,
Trust at the Core.

SaaS or self-hosted deployment

Agentless, Rapid Deployment with native-API Integration