Just-In-Time Access

Why Just-In-Time (JIT) Access?
Long-standing access privileges create vulnerabilities that put organizations at high risk. Compromised credentials subject enterprises of all sizes to threats that cause data breaches, data leaks, and data loss. This means potential lawsuits, regulatory fines and loss of customer trust.
This legacy practice of widely-approved permissions is not suitable for an agile workforce and for organizations transitioning to the cloud. On the other hand, permanently limiting permissions upsets the organization’s ability to progress.
Just-In-Time access ensures that users have access to a system or resource only for the duration of the task or action that requires it. Access is restricted to a specific purpose and revoked when the need is no longer met. Learn more.
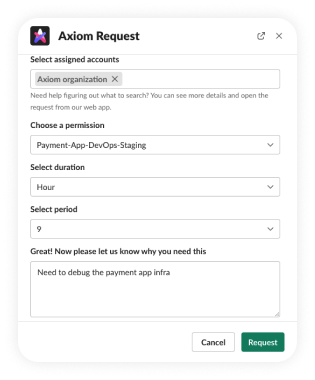
Axiom Delivers a Secure and Dynamic Approach to JIT Access
Organizations need a flexible way to grant and revoke permissions according to JIT access. But the solution many organizations have implemented is everything but flexible: they use a manual ticketing process for requesting access. This “solution” comes at the expense of employees, and, ultimately, the organization.
Employees need to move fast to get things done. Manually requesting and waiting for permissions slows everyone down and puts the organization at a competitive disadvantage.
Axiom provides an easy-to-use, automated platform for implementing JIT access in the organization:
Just-In-Time Right-Sized Access
Easily implement JIT access:
- The appropriate level of access
- When, and only when, access is needed
- No more standing privileges
- 0 productivity sacrifice
- Scale as needed
Meets Users Where They Are
Seamlessly integrate JIT access into users’ day-to-day:
- Easy-to-use self-service capabilities
- Integrate with your collaboration tool: Slack, Teams, CLI, and others
- Users request and receive or permissions and updates in their tool of choice
Intuitive and Hassle-free
JIT access at the click of a button:
- A stellar user experience
- Understandable and fun to use UI
- No more guesswork: straightforward request and approval flows based on each user’s needs
- Automation makes the process simple and streamlined
Fit For All Users
Let all audiences enjoy a frictionless experience so they can focus on their core work:
- Free developers to develop, debug, troubleshoot and release
- Allow business users to easily request access to resources
- IT, IAM, security and admins enjoy the ability to build automated workflows and easily grant and revoke permissions
- A UI fit for any technical level
Never Compromise on Security
Reduce the attack surface while promising a seamless user experience:
- Define security policies based on compliance regulations, best practices and your own guidelines
- Maintain admin discretion for complex permissions requests
- Get required context when deciding whether to approve requests (or not)
- Ensure permissions are provided according to the most advanced security principles